Strengthening Your SSH Security: A Comprehensive Guide
Protecting your server and data through secure SSH access is a fundamental aspect of cybersecurity. With the increasing reliance on remote work, ensuring robust SSH security has become more critical than ever. This guide will walk you through essential steps to safeguard your remote SSH access, enhancing your overall cybersecurity strategy.
In today's interconnected world, remote server access via SSH (Secure Shell) is a widely adopted practice. However, this convenience can expose your systems to malicious actors if proper security protocols are not implemented. By understanding the vulnerabilities associated with SSH and adopting best practices, you can significantly reduce the risks of cyberattacks and unauthorized access.
By the end of this guide, you will gain a comprehensive understanding of how to secure your SSH connections, the importance of SSH security, and practical steps to protect your systems. Whether you're a system administrator, an IT professional, or a tech enthusiast, this resource will provide actionable insights to enhance your SSH security.
Read also:Exploring Elon Musks Partners And Kids A Comprehensive Look
Table of Contents
- Understanding SSH: A Secure Communication Protocol
- The Importance of Securing SSH Access
- Common SSH Security Threats
- Best Practices for Securing SSH
- Customizing Your SSH Port for Enhanced Security
- Implementing SSH Keys for Authentication
- Disabling Root Login to Minimize Risks
- Configuring Firewalls for SSH Protection
- Monitoring SSH Activity for Suspicious Behavior
- Advanced Security Measures for SSH
Understanding SSH: A Secure Communication Protocol
SSH, or Secure Shell, is a network protocol designed to facilitate secure communication between a client and a server. It establishes a protected channel over an unsecured network, ensuring that all data exchanged remains encrypted and shielded from unauthorized access or interception.
SSH plays a vital role in remote administration, file transfers, and command execution on remote machines. Its robust encryption mechanisms make it an indispensable tool for secure communication across the internet. By leveraging SSH, users can confidently manage their systems remotely without compromising sensitive information.
How SSH Ensures Secure Communication
- SSH employs advanced encryption algorithms to establish a secure connection between the client and server.
- User authentication is achieved through passwords or public key cryptography, ensuring only authorized users gain access.
- All data transmitted over SSH is encrypted, guaranteeing confidentiality and integrity throughout the communication process.
The Importance of Securing SSH Access
Securing remote SSH access is essential for safeguarding your server and sensitive data against unauthorized access, cyberattacks, and data breaches. Without proper security measures, your systems can become vulnerable to malicious activities, compromising the integrity and confidentiality of your data.
In environments where remote access is a routine practice, whether for personal servers or corporate networks, maintaining the security of SSH connections is paramount. It ensures the reliability and trustworthiness of your systems while mitigating potential risks associated with unauthorized access.
Risks Associated with Insecure SSH Access
- Unauthorized access to confidential data, leading to potential data breaches.
- Increased susceptibility to malware and ransomware attacks, which can disrupt operations and cause significant financial losses.
- Non-compliance with industry regulations, resulting in legal consequences and damage to organizational reputation.
Common SSH Security Threats
SSH connections are susceptible to various security threats that can compromise their integrity. Recognizing these threats is the first step in implementing effective security measures to protect your systems.
- Brute Force Attacks: Hackers use automated tools to repeatedly guess passwords, attempting to gain unauthorized access.
- Man-in-the-Middle Attacks: Attackers intercept communication between the client and server, potentially altering or stealing sensitive information.
- Configuration Errors: Misconfigured SSH settings can expose your server to vulnerabilities, making it an easy target for cybercriminals.
Identifying and Addressing SSH Vulnerabilities
Regularly auditing your SSH configurations and monitoring for unusual activities can help identify potential vulnerabilities. Utilizing tools like fail2ban and intrusion detection systems can assist in detecting and mitigating threats effectively. Proactive measures are crucial in maintaining the security of your SSH connections.
Read also:Why You Should Join Wewillwritecom Today Unlock Your Writing Potential
Best Practices for Securing SSH
Implementing best practices for SSH security is essential for enhancing the protection of your remote connections. Below are some recommended strategies to fortify your SSH access and minimize risks.
1. Keeping SSH Software Updated
Maintaining the latest version of your SSH software ensures that you benefit from the most recent security patches and features. Regular updates are critical in safeguarding against known vulnerabilities and potential exploits, providing an additional layer of protection for your systems.
2. Encouraging the Use of Strong Passwords
Promoting the use of strong, complex passwords for SSH authentication is vital in preventing unauthorized access. Avoid using predictable or easily guessable passwords and consider enforcing password policies that mandate complexity requirements. Strong passwords act as the first line of defense against cyber threats.
Customizing Your SSH Port for Enhanced Security
One of the simplest yet highly effective ways to enhance SSH security is by changing the default SSH port (22) to a non-standard port. This modification can significantly reduce the number of automated attacks targeting the default port, thereby improving the overall security posture of your server.
To implement this change, modify the SSH configuration file to specify a custom port for your SSH service. Ensure that your firewall rules are updated to permit traffic on the new port, ensuring seamless communication while enhancing security.
Steps to Change Your SSH Port
- Access the SSH configuration file located at
/etc/ssh/sshd_config. - Locate the line starting with
Port 22and replace it with your desired custom port number. - Restart the SSH service to apply the changes and ensure the new configuration takes effect.
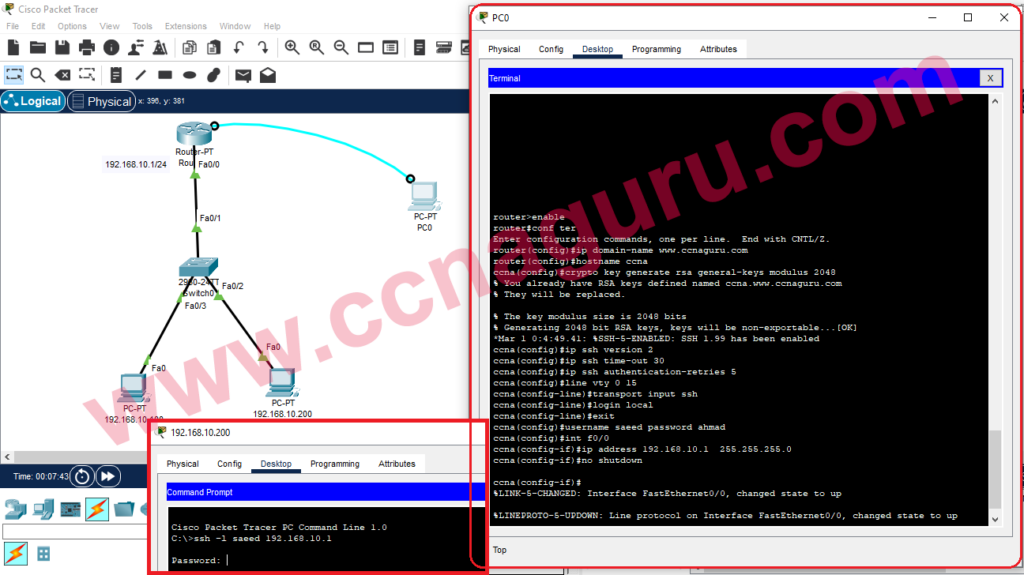
Implementing SSH Keys for Authentication
Utilizing SSH keys for authentication is a more secure alternative to traditional password-based authentication. SSH keys provide robust security by leveraging cryptographic algorithms, eliminating the risks associated with brute force attacks and unauthorized access.
To set up SSH key authentication, generate a public-private key pair and configure your server to accept key-based authentication. This method ensures that only authorized users with the correct private key can access the server, enhancing the security of your remote connections.
Benefits of SSH Key Authentication
- Eliminates the need for passwords, reducing the likelihood of credential theft and unauthorized access.
- Provides stronger security through advanced cryptographic algorithms, ensuring the confidentiality and integrity of your data.
- Facilitates seamless access without the need for repeated password entry, improving user experience while maintaining high security standards.
Disabling Root Login to Minimize Risks
Prohibiting direct root login via SSH is a critical security measure. By disabling root login, you prevent attackers from gaining immediate access to administrative privileges, even if they manage to compromise the SSH credentials. This precaution significantly enhances the security of your server.
Instead of allowing direct root access, configure your SSH settings to require users to log in with a standard account and escalate privileges using tools like sudo. This approach adds an extra layer of protection, ensuring that administrative actions are performed securely and under controlled conditions.
Steps to Disable Root Login
- Access the SSH configuration file located at
/etc/ssh/sshd_config. - Set the
PermitRootLoginparameter tonoto disable direct root login. - Restart the SSH service to apply the changes and ensure the new settings take effect.
Configuring Firewalls for SSH Protection
Configuring a firewall is an essential step in securing your SSH connections. Firewalls help regulate inbound and outbound traffic, ensuring that only authorized connections are permitted. By setting up firewall rules to restrict SSH access to trusted IP addresses or networks, you can minimize the attack surface and reduce the risk of unauthorized access.
Utilize tools like iptables or ufw to manage firewall rules effectively, ensuring that your SSH connections remain secure and protected from potential threats. Regularly reviewing and updating firewall rules to reflect changes in your network topology is crucial in maintaining robust security.
Firewall Configuration Recommendations
- Restrict SSH access to specific IP ranges or subnets, limiting the exposure of your server to unauthorized access.
- Leverage tools like iptables or ufw to create and manage firewall rules efficiently, ensuring optimal security for your SSH connections.
- Periodically review and update firewall rules to align with changes in your network infrastructure, maintaining a secure and adaptive environment.
Monitoring SSH Activity for Suspicious Behavior
Monitoring SSH activity is a critical component of detecting suspicious behavior and responding to potential threats. Implementing logging and auditing mechanisms allows you to track who is accessing your server and what actions they are performing, providing valuable insights into the security of your systems.
Tools like logwatch and auditd can analyze SSH logs and identify unusual patterns or unauthorized access attempts, enabling you to take proactive measures to address security concerns. Regularly reviewing logs and investigating any suspicious entries is essential in maintaining the integrity of your SSH connections.
Best Practices for Monitoring SSH Activity
- Enable detailed logging for SSH connections to capture comprehensive information about user activities and potential threats.
- Set up alerts for failed login attempts or unusual behavior, ensuring timely detection and response to potential security incidents.
- Regularly review logs and conduct thorough investigations into any suspicious entries, taking corrective actions as needed to mitigate risks.
Advanced Security Measures for SSH
For organizations requiring enhanced security, implementing advanced measures can further protect SSH access. Below are some additional strategies to consider for fortifying your SSH security and minimizing risks.
1. Enabling Two-Factor Authentication (2FA)
Enabling two-factor authentication adds an extra layer of security by requiring users to provide a second form of verification in addition to their SSH key or password. This approach significantly reduces the likelihood of unauthorized access, even if credentials are compromised.
2. Deploying Intrusion Detection Systems
Implementing intrusion detection systems (IDS) can help detect and respond to unauthorized access attempts in real-time. IDS tools analyze network traffic and alert administrators of potential threats, enabling swift action to mitigate risks and protect your systems.
3. Conducting Regular Security Audits
Performing regular security audits ensures that your SSH configurations remain secure and compliant with industry standards. Audits can identify vulnerabilities, recommend corrective actions, and provide valuable insights into the overall security posture of your systems.
Conclusion
Securing remote SSH access is a critical component of maintaining the security and integrity of your systems. By adhering to the best practices outlined in this guide, you can significantly reduce the risk of unauthorized access and protect your sensitive data from potential threats.
Remember to regularly update your SSH software, employ strong authentication methods, and monitor your SSH activity for any signs of suspicious behavior. Encourage your team to adopt these practices and foster a culture of cybersecurity awareness within your organization.
Take immediate action by implementing the steps discussed in this guide. Share your thoughts or ask questions in the comments below. Don't hesitate to explore additional resources on our site for more insights into cybersecurity and IT best practices.