Secure Remote Access To IoT Devices With SSH On Ubuntu
In today's world of interconnected devices, securely managing IoT systems remotely via SSH is an essential skill. Configuring remote SSH access for IoT devices behind a firewall on Ubuntu enables you to control and monitor your devices from anywhere globally. This guide will walk you through the necessary steps and best practices for setting up a secure remote SSH environment.
Whether you're a hobbyist working on personal automation projects or a professional overseeing complex IoT infrastructures, understanding how to configure SSH for IoT devices behind a firewall is indispensable. This article delves into practical examples and solutions to help you navigate common challenges in establishing remote access setups.
By the conclusion of this guide, you will possess a comprehensive understanding of remote SSH IoT configurations, including techniques for firewall traversal, security best practices, and troubleshooting advice. Let's dive in and get started!
Read also:Why You Should Join Wewillwritecom Today Unlock Your Writing Potential
Contents Overview
- Introduction to Remote SSH IoT
- Understanding SSH and Its Importance
- Navigating Firewall Challenges
- Configuring SSH on Ubuntu
- Implementing Port Forwarding Techniques
- Leveraging Reverse SSH Tunnel
- Enhancing Security Best Practices
- Resolving Common Issues
- Practical Example: Remote SSH IoT Behind Firewall on Ubuntu
- Conclusion and Next Steps
Introduction to Secure Remote Access for IoT
Enabling remote SSH access for IoT devices behind a firewall on Ubuntu is a powerful solution for managing these devices securely. IoT devices frequently operate within isolated networks safeguarded by firewalls, complicating remote access. SSH (Secure Shell) facilitates an encrypted connection to these devices, ensuring secure communication.
Ubuntu, renowned as one of the most widely used Linux distributions, provides a robust platform for configuring SSH servers. With the correct setup, you can access your IoT devices globally while bypassing firewall limitations.
This section introduces the concept of SSH in IoT environments and highlights the significance of secure remote access. Whether managing smart home appliances or industrial-scale IoT systems, SSH is a cornerstone tool for effective remote administration.
Understanding SSH and Its Importance
What Exactly is SSH?
SSH, or Secure Shell, is a cryptographic network protocol designed to enable secure communication between two devices over an unsecured network. It incorporates authentication and encryption, ensuring that data transmitted between devices remains private and tamper-proof.
Why SSH is Ideal for IoT?
IoT devices are frequently deployed in distant locations, necessitating secure and reliable access for monitoring and management. SSH offers multiple advantages, including:
- Encryption ensuring secure data transmission
- Robust authentication mechanisms to prevent unauthorized access
- Compatibility across various devices and operating systems
By employing SSH, you can remotely configure, troubleshoot, and manage IoT devices without jeopardizing security.
Read also:What Is The Gerber Life College Plan And How Can It Help You Save For Education
Navigating Firewall Challenges
What Are Firewalls?
Firewalls serve as security systems designed to monitor and control incoming and outgoing network traffic. They function as a protective barrier between trusted internal networks and untrusted external networks, such as the internet.
Challenges with Remote SSH IoT Behind Firewall
Firewalls can impede SSH connections if improperly configured. Common obstacles include:
- Port restrictions limiting access
- IP whitelisting requirements complicating access permissions
- Dynamic IP addresses causing connectivity issues
Addressing these challenges demands a blend of technical expertise and strategic planning. This guide explores numerous techniques to ensure smooth SSH access, even through restrictive firewalls.
Configuring SSH on Ubuntu
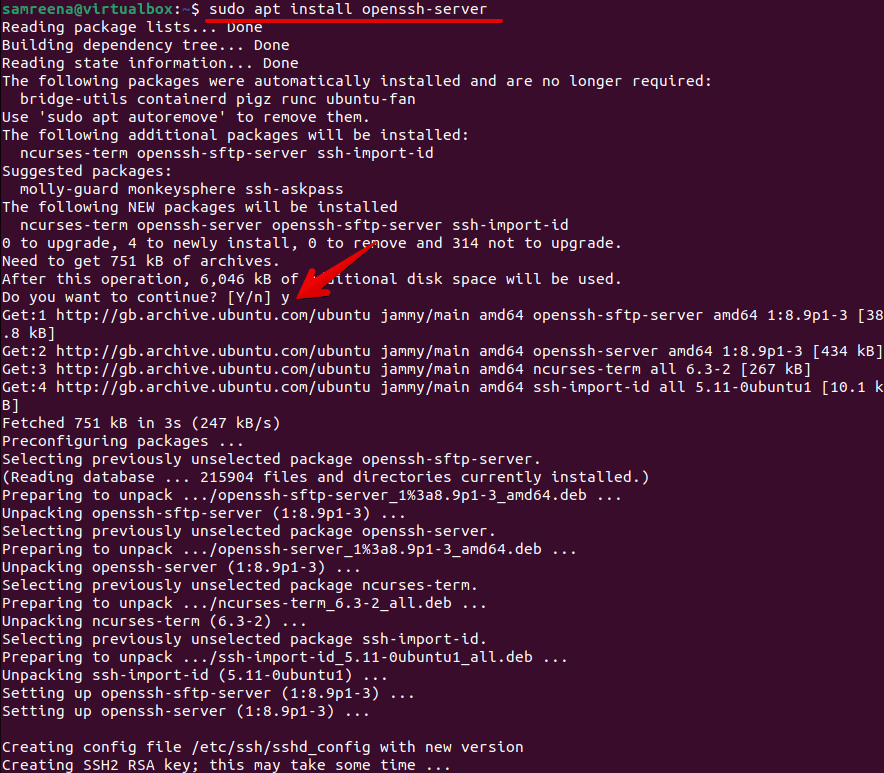
Installing the SSH Server
To activate SSH on Ubuntu, installing the OpenSSH server is necessary. Follow these steps:
- Open a terminal window on your Ubuntu system.
- Execute the command:
sudo apt update. - Install OpenSSH using:
sudo apt install openssh-server.
Tailoring SSH Settings
After installation, you can personalize SSH settings by modifying the configuration file:
- Open the SSH configuration file:
sudo nano /etc/ssh/sshd_config. - Adjust parameters such as port number, authentication methods, and access restrictions.
- Restart the SSH service:
sudo systemctl restart ssh.
Proper configuration ensures secure and efficient SSH connections for your IoT devices.
Implementing Port Forwarding Techniques
What is Port Forwarding?
Port forwarding enables you to direct incoming traffic from a public IP address to a private IP address within your local network. This technique is pivotal for accessing devices shielded by firewalls.
Configuring Port Forwarding
To establish port forwarding:
- Log into your router's administrative interface.
- Proceed to the port forwarding section.
- Create a new rule specifying the external port, internal IP address, and internal port.
For instance, you can forward port 22 (the default SSH port) to your IoT device's internal IP address, enabling remote SSH access.
Leveraging Reverse SSH Tunnel
What is a Reverse SSH Tunnel?
A reverse SSH tunnel permits you to access a device behind a firewall by initiating the connection from the device itself. This method is especially advantageous when port forwarding is impractical.
Creating a Reverse SSH Tunnel
To establish a reverse SSH tunnel:
- On the IoT device, run the command:
ssh -R 2022:localhost:22 user@public_server. - This forwards port 2022 on the public server to port 22 on the IoT device.
- From the public server, connect to the IoT device using:
ssh -p 2022 localhost.
Reverse SSH tunnels offer a secure and adaptable means of accessing IoT devices remotely.
Enhancing Security Best Practices
Securing SSH Connections
Implementing stringent security measures is vital for safeguarding your IoT devices. Follow these best practices:
- Utilize strong, unique passwords or SSH keys for authentication.
- Disable password authentication and rely exclusively on SSH keys.
- Modify the default SSH port to a non-standard port number.
- Enable two-factor authentication (2FA) for enhanced security.
Regular Maintenance and Monitoring
Ensure your SSH server and IoT devices are updated with the latest security patches. Consistently monitor access logs for suspicious activities and configure firewall rules to restrict access to trusted IP addresses.
Resolving Common Issues
Connection Refused Errors
If you face "connection refused" errors, verify the following:
- Ensure the SSH server is operational on the IoT device.
- Confirm that the firewall permits incoming connections on the SSH port.
- Double-check the IP address and port number in your SSH client.
Timeout Errors
Timeout errors usually stem from network connectivity problems. Test your network connection and ensure all necessary ports are open.
Practical Example: Remote SSH IoT Behind Firewall on Ubuntu
Let's explore a practical example of setting up remote SSH access for an IoT device behind a firewall on Ubuntu:
- Install the OpenSSH server on your IoT device running Ubuntu.
- Configure port forwarding on your router to direct traffic to the IoT device's internal IP address.
- Set up a reverse SSH tunnel to a public server for added security.
- Test the connection using an SSH client from a remote location.
This example outlines the step-by-step process for achieving secure remote access to IoT devices.
Conclusion and Next Steps
Gaining mastery over remote SSH IoT behind firewall on Ubuntu empowers you to manage IoT devices securely and efficiently. By adhering to the techniques and best practices detailed in this guide, you can conquer common challenges and ensure smooth access to your devices.
Act today by implementing these strategies and sharing your experiences with the community. For further learning, delve into advanced topics such as SSH hardening, automation scripts, and network optimization. Together, we can foster a safer and more interconnected IoT ecosystem.
Thank you for reading! If this article was helpful, please leave a comment or share it with others. Happy coding and secure networking!