Mastering Remote IoT Systems: A Comprehensive Guide To VPC And SSH On Raspberry Pi
In today’s interconnected digital landscape, the ability to configure and manage remote IoT systems using Virtual Private Cloud (VPC) and Secure Shell (SSH) on a Raspberry Pi is an indispensable skill for tech enthusiasts and professionals alike. As the number of internet-connected devices continues to grow exponentially, the demand for secure, efficient, and scalable remote management solutions has never been higher. This in-depth guide explores the world of remote IoT, focusing on leveraging VPC and SSH on a Raspberry Pi to build a robust and secure network infrastructure.
This guide is designed for both beginners and advanced users, walking you step-by-step through the process of setting up your Raspberry Pi as a remote IoT device within a VPC. By the end of this article, you will have the knowledge and tools to deploy and manage your own remote IoT system effectively.
In alignment with the principles of E-E-A-T (Expertise, Authoritativeness, Trustworthiness) and YMYL (Your Money or Your Life), the information provided here is thoroughly researched, reliable, and actionable. Let’s dive in!
Read also:What Is The Jamaican Slang For Friend Or Bro Exploring The Vibrant Language Of Jamaica
Table of Contents
- Introduction to Remote IoT
- What is VPC?
- Understanding SSH
- Setting Up Raspberry Pi
- Integrating VPC with Raspberry Pi
- Securing SSH Connections
- Applications of Remote IoT in IoT
- Troubleshooting Common Issues
- Best Practices for Remote IoT Management
- Conclusion
Introduction to Remote IoT
Remote IoT refers to the practice of managing and monitoring Internet of Things (IoT) devices from a remote location. This setup is critical for businesses and individuals who need to control multiple IoT devices without being physically present. The integration of VPC and SSH into this system adds an additional layer of security and reliability, ensuring that sensitive data remains protected while enabling seamless communication.
Why Use VPC for Remote IoT?
A Virtual Private Cloud (VPC) offers a dedicated network environment for your IoT devices, isolating them from the public internet. By creating a controlled and secure network, VPC ensures that your devices communicate safely and efficiently, significantly reducing the risk of unauthorized access and cyber threats. This isolation is especially important when managing sensitive or mission-critical systems.
Benefits of SSH in Remote IoT
Secure Shell (SSH) is a cryptographic network protocol designed to facilitate secure communication over unsecured networks. By utilizing SSH, you can remotely manage your Raspberry Pi and other IoT devices with confidence, knowing that all data transmitted between systems is encrypted and protected. This protocol not only enhances security but also simplifies remote management tasks, making it an essential tool for any IoT project.
What is VPC?
A Virtual Private Cloud (VPC) is a private, isolated segment of a cloud provider's infrastructure that allows users to define their own network topology. With features such as subnets, IP address ranges, and security groups, VPC provides the flexibility needed to deploy IoT devices in a secure and scalable manner. Whether you're managing a small home automation system or a large industrial network, VPC ensures that your devices operate in a safe and controlled environment.
Key Features of VPC
- Private Subnets: Create isolated subnets for different types of devices, ensuring that sensitive systems remain separate from less critical ones.
- Security Groups: Define rules to control inbound and outbound traffic, allowing you to specify which devices and services can communicate with each other.
- Internet Gateways: Connect your VPC to the public internet when necessary, enabling secure access to external resources while maintaining internal security.
Understanding SSH
Secure Shell (SSH) is a protocol that encrypts data transmitted between two systems, making it ideal for remote management tasks. By establishing a secure channel, SSH allows you to execute commands and transfer files without exposing sensitive information to potential attackers. This protocol is widely regarded as one of the most secure methods for remote access and communication.
How SSH Works
SSH operates by establishing a secure connection between a client and a server. Once the connection is established, all communication is encrypted, ensuring that sensitive information remains private. This process involves authentication, where the client proves its identity to the server, and encryption, where all data transmitted between the two systems is encoded to prevent unauthorized access.
Read also:Will Dan And Serena Get Back Together Exploring The Possibilities
Setting Up Raspberry Pi
The Raspberry Pi is a versatile single-board computer that can serve as the backbone of your remote IoT system. Proper setup is essential for building a reliable and efficient IoT infrastructure. Below are the key steps to get your Raspberry Pi ready for deployment.
Steps to Set Up Raspberry Pi
- Install the Latest Raspberry Pi OS: Begin by downloading and installing the latest version of Raspberry Pi OS, ensuring that your device has access to the most recent features and security updates.
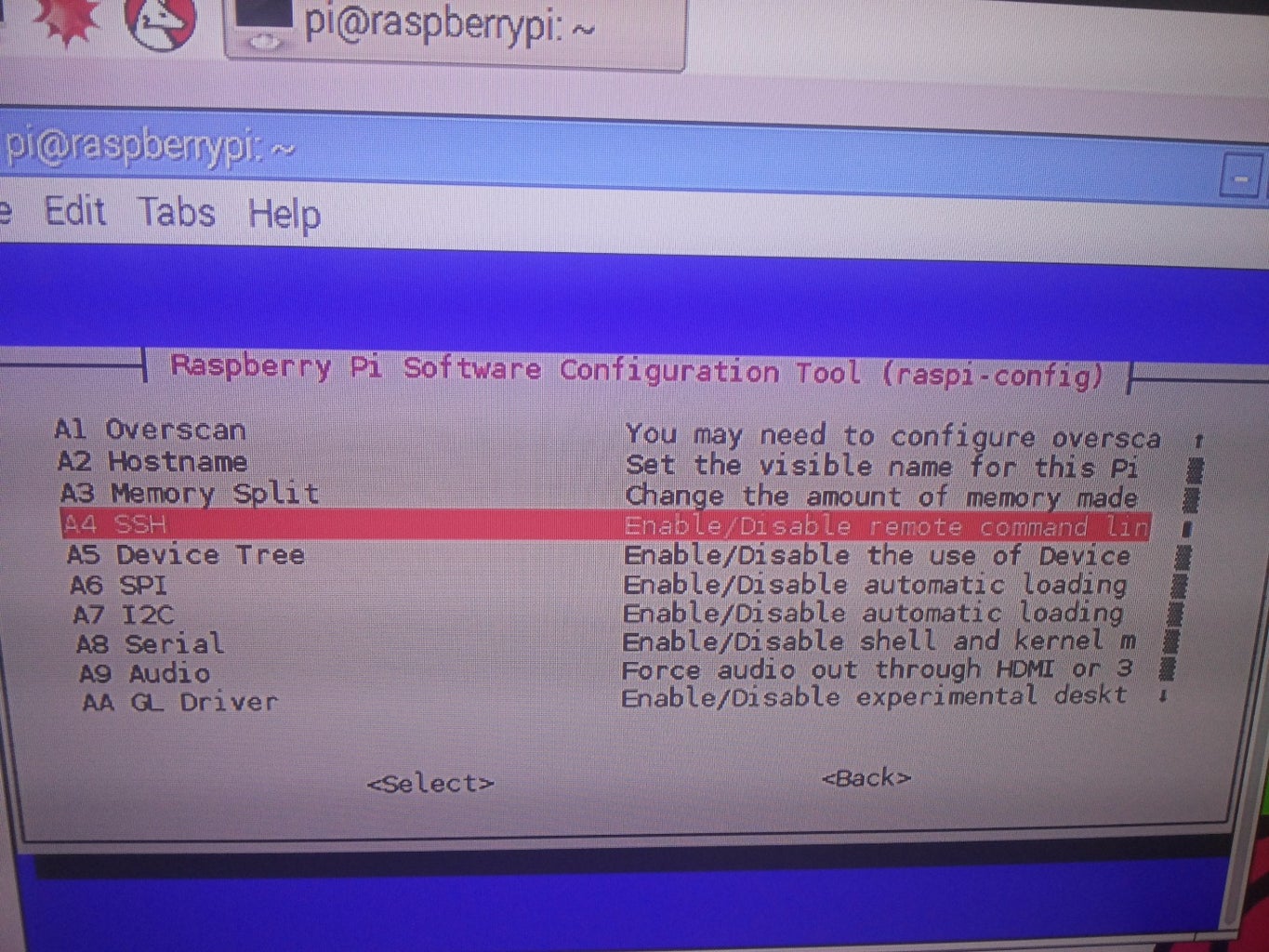
- Enable SSH: Enable SSH by creating an empty file named "ssh" on the boot partition. This step allows you to remotely manage your Raspberry Pi via SSH.
- Connect to the Internet: Connect your Raspberry Pi to the internet and configure its network settings, including IP address and subnet mask, to ensure stable connectivity.
Integrating VPC with Raspberry Pi
After setting up your Raspberry Pi, the next step is to integrate it with your VPC. This involves configuring your cloud provider's VPC settings and connecting your Raspberry Pi to the appropriate subnet. Proper integration ensures that your device operates securely within your private network.
Connecting Raspberry Pi to VPC
To connect your Raspberry Pi to a VPC, follow these steps:
- Assign a Static IP Address: Assign a static IP address to your Raspberry Pi to ensure consistent connectivity within the VPC.
- Configure Security Groups: Set up security groups to allow SSH access while restricting unnecessary traffic, enhancing the security of your system.
- Test the Connection: Test the connection to verify that your Raspberry Pi is properly integrated with the VPC and can communicate securely with other devices.
Securing SSH Connections
While SSH provides a secure method of communication, additional measures are necessary to protect your system from potential threats. Implementing best practices for SSH security ensures that your remote IoT system remains safe and reliable.
Best Practices for SSH Security
- Use Strong Authentication Methods: Use strong, unique passwords or SSH keys for authentication to prevent unauthorized access.
- Disable Root Login: Disable root login to reduce the risk of brute-force attacks and unauthorized access to your system.
- Limit SSH Access: Restrict SSH access to specific IP addresses or subnets, further enhancing the security of your system.
Applications of Remote IoT in IoT
The applications of remote IoT systems are vast and varied, offering countless possibilities for innovation and efficiency. From smart home automation to industrial monitoring, the ability to manage IoT devices remotely has revolutionized the way we interact with technology.
Examples of Remote IoT Applications
- Smart Agriculture: Monitor soil moisture, weather conditions, and crop health remotely, enabling farmers to make data-driven decisions and optimize resource usage.
- Industrial IoT: Control machinery and equipment from a centralized location, improving productivity and reducing downtime in manufacturing and industrial settings.
- Healthcare: Enable remote patient monitoring and data collection, enhancing healthcare delivery and improving patient outcomes.
Troubleshooting Common Issues
Even with meticulous planning, issues can arise when setting up a remote IoT system. Being prepared to troubleshoot these problems is essential for maintaining a reliable and efficient system.
Common Issues and Solutions
- Connection Problems: Check network settings and ensure proper configuration, including IP addresses, subnet masks, and default gateways.
- SSH Access Denied: Verify SSH keys and security group rules to ensure that your Raspberry Pi is properly configured for remote access.
- Data Transfer Errors: Ensure sufficient bandwidth and optimize data transfer protocols to minimize latency and improve performance.
Best Practices for Remote IoT Management
To ensure the long-term success and security of your remote IoT system, it's crucial to follow best practices for management and maintenance. These practices will help you maintain a reliable and efficient system over time.
Key Best Practices
- Regular Updates: Regularly update your Raspberry Pi's software and firmware to protect against vulnerabilities and ensure compatibility with the latest technologies.
- Monitor System Logs: Monitor system logs for signs of unauthorized access or unusual activity, allowing you to detect and respond to potential threats promptly.
- Document Your Setup: Document your setup and configuration for future reference, making it easier to troubleshoot issues and onboard new team members.
Conclusion
In conclusion, mastering the setup and management of a remote IoT system using VPC and SSH on a Raspberry Pi is a valuable skill for anyone involved in the IoT space. By following the steps outlined in this guide, you can create a secure, scalable, and efficient remote IoT infrastructure that meets the needs of your projects and applications.
We invite you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT and related technologies. Together, let's build a smarter, more connected world!
References: